
- Ransomware
- 8 min read

In the healthcare industry, the integration of Internet of Things (IoT) devices has ushered in numerous benefits, ranging from streamlined patient care to improved operational efficiency. However, with these advancements comes a pressing concern: the security of IoT devices and its direct impact on patient safety, as well as a whole host of other cyber security risks and threats.

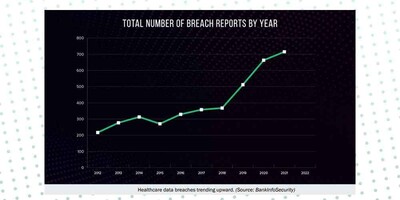
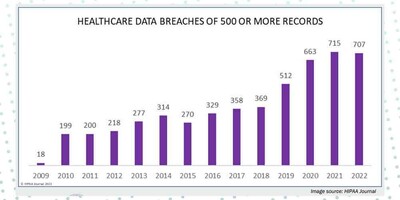
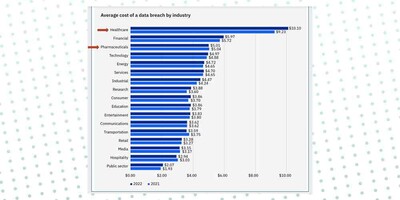
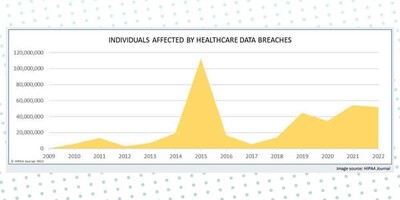
In fact, healthcare data breaches have consistently trended upward from 2012–2021, with the number of data breaches doubling in between 2019 and 2022. IBM released their Cost of a Data Breach report and for the 13th year in a row, the health sector had the highest costs for a data breach. The average breach in healthcare increased by nearly $1M and is now $10.1M. Costs have also increased over 40% in the last two years. In total, according to the United States (US) federal records, healthcare breaches have exposed 385 million patient records from 2010 to 2022.
As a security decision maker, understanding the risks and implementing robust security measures is critical. In this comprehensive blog post, we will delve into the challenges posed by IoT device vulnerabilities, real-world examples of cyber-attacks in healthcare, and strategies to ensure patient safety through effective cyber security awareness.
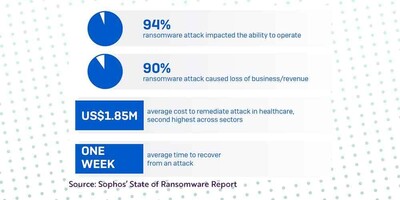
According to Cynerio and Ponemon Institute's “The Insecurity of Connected Devices in Healthcare 2022” survey, 56% of respondents have encountered at least one cyberattack involving connected devices over the last two years.
While IoT devices offer unprecedented opportunities for remote monitoring, data collection, and diagnostics, they also introduce vulnerabilities that can be exploited by cyber criminals. With the integration of various connected devices, including wearables like patient tracking wristbands and critical medical equipment like pacemakers and ventilators, ensuring the security of these devices becomes crucial.
Here are a few key challenges:
1. Comprehensive risk assessment: Conduct a thorough risk assessment to identify vulnerabilities associated with IoT devices and your general security structure. A comprehensive risk assessment allows you to evaluate potential attack vectors, unsafe behaviours, impact on patient care, and the regulatory implications of breaches. TSC’s dynamic Security Awareness and Behaviour Research (SABR) tool can assess the levels of awareness and knowledge of your workforce across five dimensions, analyse the behaviours of employees in these five dimensions, and provide an in-depth analytical report of your organisation’s security maturity. Organisations have been working with us for over 20 years deploying the SABR tool to determine their baseline results and establish and implement a plan to further develop their security maturity. By pinpointing undesirable behaviours and targeting issues at their root, TSC’s SABR assessment can inform a more effective and efficient security culture.

2. Implement Robust Authentication: Require strong, unique passwords and Multi-Factor Authentication (MFA) for IoT devices. Make sure your employees are not using the same password across numerous accounts and that they are regularly update passwords. You must ensure your employees understand the power of the password; use the real-world cyber breach examples we have listed above to provide context and hammer home the real-life ramifications of lax password behaviours.
3. Regular patching and updates: Keep devices and software updated with the latest security patches to address known vulnerabilities. Develop a schedule for regular updates and ensure compatibility with legacy systems. Not only do you need to implement a patch/update calendar, but you also need to train employees to be proactive in updating their hardware and software; you want them to take ownership of their security and, as a result, the organisation’s security.
4. Network segmentation: Isolate devices from critical patient data networks to minimise the potential impact of a breach and segment your network to confine cyber breaches to its initial entry point. Network segmentation limits attackers' lateral movement and reduces the risk of data exposure. Furthermore, because a cyber-attack on a healthcare organisation can cripple entire systems, network segmentation can ensure that total shutdowns do not occur, meaning less surgeries are postponed, and less patient data is compromised.
5. Training and awareness: You must educate healthcare staff about, password security, remote working, the risks of IoT devices, phishing, ransomware and other common cyber risks and threats. You must train them to recognise signs of potential compromise and encourage a culture of reporting any unusual activities before they develop into something really damaging. TSC offers a whole host of eLearning courses, games, and physical materials on the aforementioned cyber threats, as well as so much more. Furthermore, as creators of bespoke training and awareness materials, we can create specific materials for your organisation, for specific departments and even for specific threats.

6. Regular backups and the 3-2-1 rule: Robust data backup systems are crucial to restore operations in the event of a cyber-attack. Healthcare organisations are encouraged to establish and maintain secure data backup practices. Consider the 3-2-1 backup rule as a solution to data protection. The 3-2-1 rule is a widely recognised and recommended approach for creating comprehensive data backups that ensure data availability, security, and recovery in case of data loss or disasters. The rule advises organisations to maintain 3 copies of your data, to store those copies on 2 different types of media, and to keep 1 copy off-site, ideally in a different geographical location. The 3-2-1 backup rule provides a strong balance between data availability, redundancy, and protection against various types of risks. Following this rule helps ensure that you have multiple layers of protection for your data and can recover it in case of unexpected events.
Faced with this reality and this snapshot of current threats, it is increasingly important to engage your workforce in their role within a strong line of defence against cyber-attacks.
Training and awareness are fundamental in enabling people to provide that line of defence. However, training alone will not provide the behaviour change that is required from every employee.
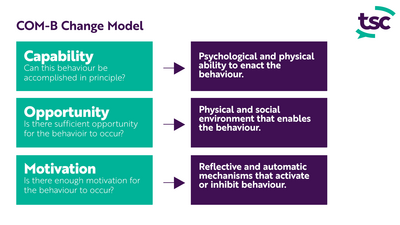
Understanding the factors that can influence behaviours are the key to behaviour change. The COM-B model of behaviour change, used by The Security Company, proposes that to engage in a behaviour (B - Behaviour) at any given moment, a person must be physically and psychologically able (C - Competence or Capability) and have the opportunity (O - Opportunity) to exhibit the behaviour, as well as the want or need to demonstrate the behaviour at that moment (M - Motivation).
Our behaviour change research shows that an individual’s behaviour will change if all the elements above – capacity, opportunity, and motivation – are successfully implemented. We combine these three sources of behaviour with our behaviour change wheel to provide a systemic overview for your organisation of your current security culture. Let us chat to discuss how leveraging behavioural theories can significantly enhance your efforts to bolster IoT device security.
Cyber security awareness and training is crucial in healthcare to mitigate the risks of cyber threats, protect patient data, and ensure the continuity of patient care. It helps employees recognise and respond to potential threats, reducing the likelihood of successful cyber-attacks.
Effective methods include interactive team activities, workshops, simulated phishing exercises, gamification, engaging eLearning courses and bespoke role-based training. These methods will help you engage employees across generations, departments, and learning styles whilst providing hands-on experience in recognising and responding to threats.
Regular training is essential. Basic training on cyber threats like phishing and password security should be conducted bi-annually but refreshed regularly throughout the year with awareness materials like physical posters, email signatures, GIFs, and games. However, if you conduct a security assessment, you will gain more insight into how often and what security training you need to implement. One solution does not apply to all organisations, whilst a personal and bespoke solution will be far more effective.
Yes, cyber-attacks on IoT devices can have immediate consequences on patient care. For example, attacks on medical devices can lead to service disruptions, delays in treatment, and compromised patient data. This can have massive medical, financial, and regulatory ramifications.
The FDA (Food and Drug Administration) recommends manufacturers use the NIST (National Institute of Standards and Technology) Framework for Improving Critical Infrastructure Cyber security, which builds on earlier guidance for Industrial Control Systems. The Healthcare Cyber security Act of 2022 requires the Cyber security and Infrastructure Security Agency (CISA) and the U.S. Department of Health and Human Services (HHS) to collaborate around improving cyber security in the healthcare and public health sectors, with CISA charged with the specifics. Part of this act includes a detailed study on cyber security risks for the health sector, and how to manage these risks with a shortage of qualified cyber security workers. CISA would be responsible to make resources, including cyber-threat indicators and appropriate defence measures, available to federal and non-federal entities that receive information through HHS programs. Furthermore, the US has also introduced the Protecting and Transforming Cyber Health Care Act, the PATCH Act. This law is specifically focused on new requirements for medical device and network security, setting cyber security requirements for medical device manufacturers by requiring premarket approval through the Food and Drug Administration, requiring development of plans to identify and address post-market cyber security vulnerabilities, and also allowing manufacturers to design, develop and maintain processes and procedures to update and patch devices and related systems throughout lifecycles.
In the EU, the Medical Device Regulation (MDR) emphasises cyber security as a component of medical device safety. In the UK, the NHS has released device security guidance and, on June 2022, they released a report on the future regulation of medical devices in the United Kingdom in a post-EU Britain.
In the healthcare sector, the potential benefits of IoT devices are vast, but so are the risks they introduce, and this is not even considering numerous other threats such as ransomware, phishing, and poor password security. In the past year, we even saw an alarming 63.5% of phishing domains masquerading as websites of healthcare organisations, down utilising the HTTPS protocol to deceive victims by exploiting the trust of the little padlock icon typically associated with secure connections.
By understanding the challenges, leveraging behavioural insights, and implementing comprehensive strategies, you can establish a resilient defence against cyber threats. Many security leaders in the healthcare space are waking up the music, which may explain why the global healthcare cyber security market size is estimated to rise from US$ 17.35 billion in 2022 to around US$ 81.63 billion by 2032, according to Precedence Research.
You simply cannot afford to be left behind!
Remember, a well-informed and security-conscious healthcare environment is the cornerstone of patient well-being in the digital age.
If you would like information about how The Security Company can help you to formulate a cyber security training and awareness program for your healthcare organisation or if you would like a demo of our SABR tool to identify gaps in your security armour ... please contact our Head of Business Development and Sales, Jenny Mandley.
The Security Company's vast library of customised and non-customised products and services are tailored for small, medium and large organisations and are available in a variety of languages. We also offer bespoke solutions for organisations that desire training and awareness materials built from the ground up.



© The Security Company (International) Limited 2025
Office One, 1 Coldbath Square, London, EC1R 5HL, UK
Company registration No: 3703393
VAT No: 385 8337 51


