
- Ransomware
- 8 min read


Whilst global support is often empathetic and rapid, cyber criminals see natural disasters as an opportunity to take advantage of the situation and exploit victims.
Maria Thompson, North Carolina’s Chief Risk Officer’s words after Hurricane Florence in 2018 remains very apt to this day: “Be cautious and stay vigilant. Let’s ensure one disaster does not lead to another. Cyber criminals will use every tactic in their arsenal to deprive citizens of their information and ultimately their financial assets.”
Today, we will explore how cyber criminals can take advantage of natural disasters, as well as how individuals and organisations can protect themselves.
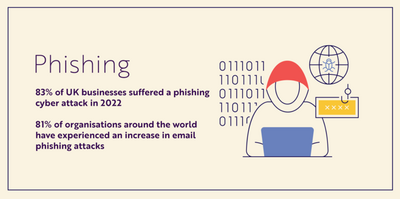
The primary way cyber criminals take advantage of natural disasters is through phishing scams. One of the most common cyber threats, threats actors use deceptive emails and texts – and in some cases phone calls – to trick individuals into releasing sensitive information or compromise their hardware via a malicious link.
After a natural disaster has occurred, cyber criminals understand that the focus and priority of essential services is focused elsewhere. As a result, they send out phishing emails that purport to be a legitimate charity or relief organisation. These emails will prompt for donations or personal information using the guise of legitimate organisations through well designed fake emails.
This is why at TSC we value the importance of teaching individuals the signs of a phishing scheme. Whilst many of us are kind-hearted and happy to help in dire situations like this, cyber criminals are betting on that sentiment to trick you. We must always verify the legitimacy of any communication before submitting money or personal information.
[DOWNLOAD OUR FREE EBOOK ON PHISHING]
Natural disasters also bring malware attacks. Malware, malicious software that infects computer systems with the intention to damage or steal information, is used against targets that are now significantly more vulnerable because of a disaster.
For example, a threat actor could set up an infected website or social media link under the guise of offering disaster relief. When a vulnerable organisation or individual falls for this, they unknowingly invite malware onto their network and cyber criminals pillage whatever is left.
A far more sadistic use of malware in these situations is to use malware to target organisations that are helping with relief efforts. Here, by infecting helpers, cyber criminals can disrupt relief efforts and cause even more human and economic loss with cyber crime.
[DOWNLOAD OUR FREE EBOOK ON MALWARE]
Cyber criminals have also been known to use natural disasters as an opportunity to run ransomware attacks. When a natural disaster hits, depending on what it is and how damaging the ramifications are, many organisations will not have their optimum security layers in place, some may even be gone or destroyed for good and others will be focused on recovery efforts not security measures.
This is an opportune time for threat actors to run a ransomware attack as the natural disaster and relief efforts works as a cover for their activities, making it extremely difficult for victims to detect an attack, let along respond or even prevent it.
Cyber criminals understand that the 9/11 attacks are one of the most painful and impactful attacks in US history. They also understand that nearly every single American has a strong feeling about the attacks and are willing to exploit that. Whenever an anniversary date rolls around, threat actors take it as an opportunity to run phishing scams. In fact, this is something that has been picked by the DHS (Department of Homeland Security) who state most cases revolve around fake websites gleaming real donations. Fraudsters have no shame and they will ask for money to support victims or the families of those killed during 9/11. This shows you the psychological aspect of running cyber attacks related to disasters as threat actors prey on people’s emotional side.
In 2009, we encountered an influenza pandemic that lasted for over 19 months affecting between 700 million and 1.4 billion people. One of the effects of swine flu was creating communities of people that were deeply frightened of catching the H1N1 flu virus and another community of people looking for quick and easy cures. As a result, scammers were quick to create fake treatments such as useless hand sprays that claimed to kill the virus. Official authorities like the FDA (Food and Drug Administration) had to be quick to stamp out these opportunistic threat actors but some vulnerable, gullible individuals were taken advantage of. Here threat actors used a combination of social engineering and spamming phishing messages to exploit people.
In 2010, Haiti was hit with an earthquake that affected over 3 million Haitians and killed over 300,000 people. Threat actors used this devastating natural disaster to get creative and exploit the disaster. They created fake websites, social media posts and emails asking for donations that went to fraudulent charities. They also indulged in SEO poisoning; this is where malicious websites are pumped to the top of search engine results using SEO tactics. So, even if you were innocently looking for a way to help with the relief efforts, you may unwittingly have donated to a fraudulent link because threat actors gamed the search engine.
In 2011, an 8.9 magnitude earthquake was recorded off the coast of Japan, which resulted in a massive tsunami hitting the Pacific region. Using the same tactics we saw during the Haiti earthquake the year prior, cyber criminals set up SEO traps leading both victims and individuals looking to help towards malicious and phony websites teeming with malware. In this instance, one prominent cyber criminal infected many individuals and organisations with FAKEAV malware. Cyber criminals also flooded social media with links labelled ‘Shocking news’ or ‘Shocking video,’ which when clicked unleashed malware.
In 2014, all major news sites and public interest was focused on MH17, a passenger flight from Amsterdam to Kuala Lampur that was hit by a ground-to-air missile. It was around this time that the rate of sharing news stories catapulted on both social media platforms and text messaging services. Cyber criminals used this opportunity to spread malicious links to vulnerable, less-tech-savvy, individuals via messaging services such as Facebook and WhatsApp. Elderly groups and individuals who have never been taught or aware of cyber threats were the primary targets as they are known to share and consume news stories via shared article links.
In August 2017, a Category 4 hurricane made landfall on Texas and Louisiana, leading to devastating floods and many deaths. US-CERT (United States Computer Emergency Readiness Team) knew cyber criminals would use this as an opportunity to contact vulnerable and desperate individuals. Perhaps learning from past disasters, US-CERT sent out a warning asking everyone to stay vigilant to any messages or links claiming to be related to Hurricane Harvey and to always verify. And whilst we saw a 419% increase in phishing attacks during Hurricane Harvey, US-CERT’s may have caused criminals to get even more creative. Some threat actors started to scrape social media to find individuals who had relatives in affected areas to manufacture very personal social engineering content. Instead of receiving emails asking for a general donation, a cyber criminal may have found the name of a cousin that had been affected and included that to prey on your emotions!
Hurricane Harvey inspired Houston city officials and the US Army Cyber Institute to run a three-day drill one year later simulating a cyber attack amid a hurricane. Houston Mayor Sylvester Turner said: “Our city is the ideal location to conduct this research to prevent, protect, mitigate, respond, and recover from threats and hazards that affect not only our community but the impacts they have on the nation’s critical infrastructure.
In 2019, over 50 people were killed in a mass shooting in a Christchurch Mosque. Showing that they have no morals or shame, cyber criminals used this as an opportunity to make money. By spoofing Westpac, one of Australia’s major banks, cyber criminals sent out fake emails asking for donations to help victims. Because of the high emotions running at the time and the apparent legitimacy of Westpac, cyber criminals were successful. In fact, New Zealand’s Computer Emergency Readiness Team (CERT NZ) stated that whilst over NZ$ 7 million was donated, they cannot confirm if even half of that actually reached official and legitimate authorities.
Whilst tens of thousands of people lost their lives to a devastating earthquake, cyber criminals are still exploiting vulnerable situations. Bitdefender Antispam Lab have uncovered a host of different scams being run to exploit the situation. The first is using a fake Ukrainian charity called the ‘Wladimir Foundation’ to trick users into donating for the relief effort. This particular attack was focused on South Korea, Vietnam, the US, India, Denmark, Ireland, Germany, and the UK with scam emails originating from IP addresses in Pakistan. Another is sending spoof UNICEF emails from IP addresses in Germany and Malaysia and is specifically targeting UK and US individuals.

If we analyse the most common cyber attacks that we see post natural disasters and some of the examples of cyber attacks over the years, we can put together a list of behaviours we should all stick to in these situations. Granted, a traumatic and hectic situation amplifies human errors and security may be the last thing on your mind, but you must understand cyber criminals are hoping you do not care … do not fall for it!

If there is a chance of profit, cyber criminals and threat actors will not give a second thought to exploiting your emotions, even if you find yourself in a life-or-death situation. If there is a possibility of financial gain, they will take advantage of the situation even if it leads to even more loss of human life.
However, cyber crime during crises highlights a key fundamental of cyber security: as humans are at the centre of most attacks, they must also be at the centre of the solution!
You never know what’s around the corner for your community or your organisation. An effective security system not only considers hardware fundamentals but also includes effective security education and awareness training at all levels of your organisation. You want to arm your employees to stay security strong even in emotionally vulnerable situations. Hopefully, the devastating list of case studies above can provide some needed context on how cyber criminals still find a way to worsen the effects of a disastrous event.
If you would like more information about how The Security Company can help your organisation and deliver security awareness training and employee development for you ... or how we can run a behavioural research survey to pinpoint gaps in your security culture, please contact Jenny Mandley.



© The Security Company (International) Limited 2025
Office One, 1 Coldbath Square, London, EC1R 5HL, UK
Company registration No: 3703393
VAT No: 385 8337 51


