
- Employee awareness
- 5 min read

Understanding the dark web is crucial for all businesses, security teams and employees. It's a shadowy corner of the internet where anonymity reigns supreme and nefarious activities thrive.
In this article, we'll delve into what the dark web is, its implications for cyber threats, and most importantly, how cyber security training and awareness can help mitigate the risks associated with it.
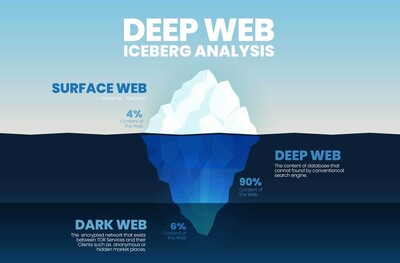
To understand the dark web, it's crucial to grasp its relationship with the broader internet landscape. Imagine the internet as an iceberg, with the surface web representing the tip visible above the waterline. This surface web is where most of our online activity occurs, including browsing websites indexed by search engines like Google or Bing – so, nothing malicious at all.
Beneath the surface lies the deep web, comprising content not indexed by traditional search engines. This includes sensitive data like personal emails, online banking information, and private databases. While the deep web is vast, it's not inherently nefarious; it simply encompasses anything not easily accessible through a search engine.
Deeper down at the sea floor, you will find the dark web; a clandestine network accessible only through specialised software like Tor (The Onion Router). Unlike the surface and deep web, the dark web operates on overlay networks and utilises onion routing to hide users' identities and locations. Websites on the dark web typically use .onion domains, which aren't indexed by search engines, further shrouding their existence.
The dark web's allure lies in its anonymity and unregulated nature. It's a digital Wild West where users can operate with impunity, shielded from the prying eyes of law enforcement and surveillance. While not inherently malicious, the dark web has garnered a reputation as a hub for illicit activities due to its anonymity-centric architecture.
Collectively, these features contribute to the dark web's enigmatic aura, fostering an environment where anonymity reigns supreme, and illicit activities flourish. While not all dark web users engage in criminal behaviour, the platform's architecture and infrastructure provide fertile ground for cybercrime and illicit transactions.
The dark web's clandestine nature and anonymity-centric architecture create a fertile breeding ground for a wide array of cyber threats.
Collectively, these implications underscore the multifaceted nature of cyber threats emanating from the dark web. From the sale of stolen data and malware to the recruitment of insiders and the proliferation of forged information, the dark web serves as a nexus of digital malevolence, fuelling a continuous cycle of cybercrime and exploitation. Understanding these implications is essential for organisations and individuals seeking to bolster their cyber defences and mitigate the risks posed by the dark web.
The dark web presents a formidable challenge to cyber security, but it's not insurmountable. Through education, vigilance, and proactive measures, individuals and organisations can mitigate the risks posed by this shadowy underworld.
Partnering with a trusted cyber security training and awareness company, such as The Security Company Ltd. (TSC), is crucial. With 25 years of experience, TSC specialises in enhancing security behaviours, fostering a robust security culture, and raising awareness of threats and risks across global organisations.
The dynamic nature of cyber threats necessitates a comprehensive and adaptive cyber security strategy for UK law firms. By understanding the evolving threat landscape and investing in robust training and awareness initiatives, decision-makers can fortify their organisations against potential risks and cyberattacks.
At The Security Company, we specialise in boosting cyber awareness, targeted training, customised projects and role-based solutions. Through our tailored subscription services, targeted and customised eLearning and awareness materials and our behavioural assessments, we're committed to helping organisations like yours instil long-term, security-conscious behaviours.
Our method is distinct. We begin by diving deep into your team's current mindset, pinpointing lax behaviours, security gaps and departments in need of focus and attention. From there, we craft tailored solutions that encourage better cyber practices from your employees. With comprehensive training and seamless integration into your current systems, we're here to fortify your team against modern cyber threats and be your trusted cyber security and awareness partner.
Ready to take the next step?
We can help you to formulate an effective and comprehensive cyber security training and awareness program for your organisation year-round and be your dedicated partner for employee behaviour change and, ultimately, security culture change.
Do not hesitate to contact us for further information.



© The Security Company (International) Limited 2023
Office One, 1 Coldbath Square, London, EC1R 5HL, UK
Company registration No: 3703393
VAT No: 385 8337 51


